Welcome to
A New Era of Security
We offer the best ICT services and cybersecurity solutions across the world. As the world changes every day in technology, rest assured we will advise and supply the best and most recent technologies.


Security Audits
Xilinxtech is known for performing the best security audits for organizations. Contact us for more information
Vulnerability Prevention
We perform Vulnerability Assessment and Penetration (VAPT) for organizations
Security Analysis
Sit back and let us give you a piece of mind. we will give expert security analysis to your organization.

About
Security Solutions & Services
Security solutions and services refer to a wide range of measures, technologies, and professional offerings designed to protect individuals, organizations, and their assets from various security threats. These threats can include physical risks, such as theft or vandalism, as well as digital risks, such as cyber attacks and data breaches.
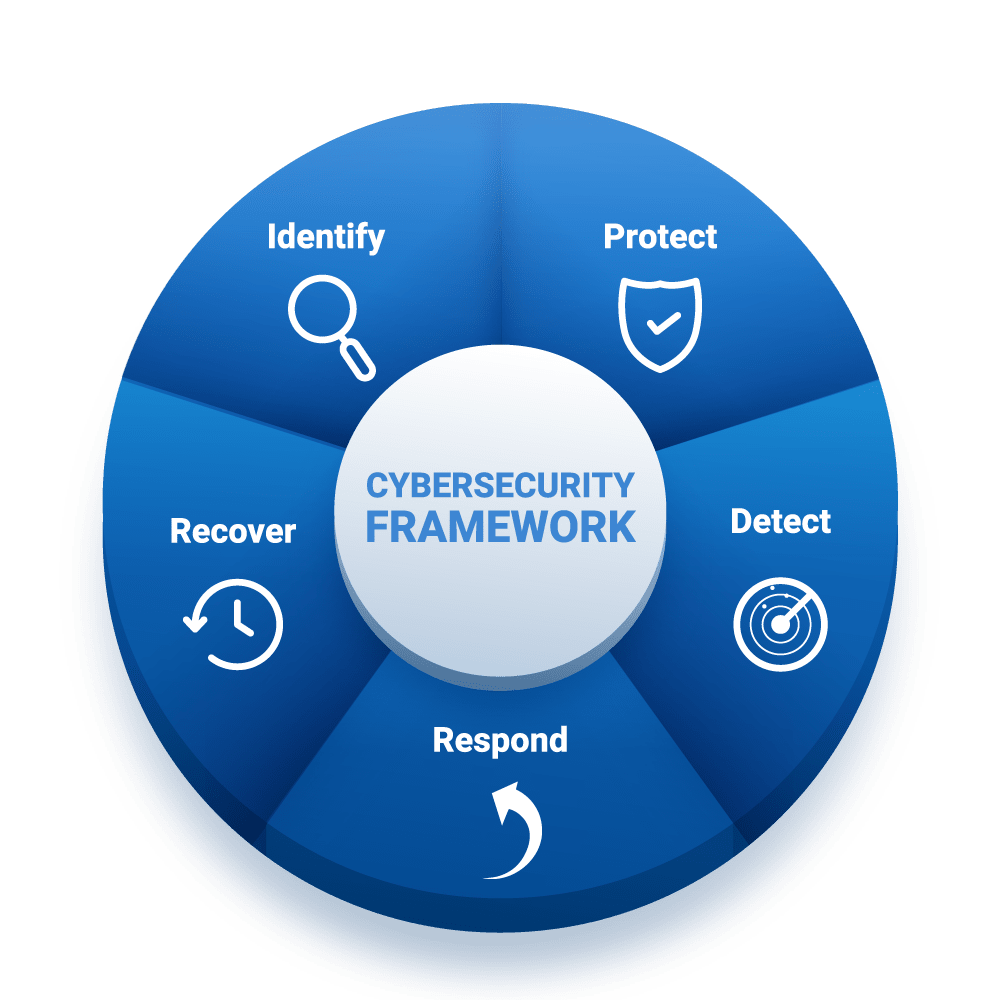
Our Cyber Security Framework
Xilinxtech will Identify, Detect, Respond, Protect, Respond, and recover. Following our frameworks guarantees 24/7 protection against cyber threat attacks.
Features
What We Offer
We offer wide range of measures, technologies, and professional offerings designed to protect individuals, organizations, and their assets from various security threats. These threats can include physical risks, such as theft or vandalism, as well as digital risks, such as cyber attacks and data breaches.
Physical Security Solutions
These involve the use of physical measures to secure premises, assets, and people. Examples include surveillance cameras, access control systems, alarms, security guards, and perimeter fencing
Security Consulting
Security consulting services involve assessing an organization’s security risks and providing recommendations to mitigate those risks. Consultants may offer expertise in physical security, cybersecurity, risk management, and compliance with regulations.
Security Monitoring and Surveillance
These services involve continuous monitoring of physical and digital environments to detect and respond to security incidents. This can include 24/7 security operations centers (SOCs) that monitor security alerts and respond to threats.
Approach
Our Approach to Security
When it comes to a comprehensive approach to cybersecurity, it’s important to consider various aspects to protect systems, networks, and data from unauthorized access, attacks, and vulnerabilities. Here are some key components of a robust cybersecurity approach:
Security Policies and Procedures
Develop and enforce a set of security policies and procedures that outline best practices, acceptable use of systems, data handling guidelines, incident response protocols, and other relevant guidelines. Regularly update and communicate these policies to all employees.
Secure Network Architecture
Implement robust network architecture with proper segmentation, firewalls, intrusion detection systems, and other security measures. Regularly update and patch network devices and software to mitigate known vulnerabilities.
Access Control
Implement strong authentication mechanisms, such as two-factor authentication, to control access to systems and sensitive data. Limit access privileges to only those necessary for employees to perform their tasks.
Continual Improvement
Cybersecurity is an ongoing process. Stay up to date with the latest security trends, emerging threats, and best practices. Continually evaluate and enhance your security controls, technologies, and procedures to adapt to evolving risks.
Risk Assessment
Begin by conducting a thorough assessment of your organization’s assets, identifying potential vulnerabilities, and evaluating the risks associated with them. This assessment helps prioritize resources and efforts for effective cybersecurity measures.
Employee Training and Awareness
Educate employees about cybersecurity best practices, such as creating strong passwords, recognizing phishing attempts, avoiding suspicious links or downloads, and reporting security incidents. Regular training sessions and awareness campaigns can help foster a security-conscious culture.
Data Encryption
Encrypt sensitive data, both in transit and at rest, using industry-standard encryption algorithms. This ensures that even if the data is compromised, it remains unreadable without the encryption key.
Incident Response Plan
Develop a detailed incident response plan that outlines the steps to be taken in the event of a cybersecurity incident. This plan should include incident identification, containment, eradication, and recovery procedures, as well as communication and reporting protocols.

Contact Us
+254 724159997
Eden Square, 5th Floor, Waiyaki Way
Monday-Friday: 8am – 5pm